If you’re involved in or using any form of SaaS, you’ve probably heard of the terms “Single Sign On (SSO)” and/or “SSO best practices.” But, what exactly are they and how do they enable your organization? Read on to find out, and
What is a Single Sign On (SSO)?
Single Sign On is an authentication service that grants a user simultaneous access to several software services by inputting a single login credential (hence the name). Most SSO services will only require a user to sign in once, meaning the user will not need to re-verify their authentication factors moving forward.
Why Does This Matter?
It may appear as though SSO is just a fancy password manager, but that’s far from the case. Many SSO solutions like Okta, Onelogin, and Bitium add an additional layer of security and control to your organization’s SaaS login process.
This means, with the growing number of SaaS applications being used by organizations, implementing an SSO has become imperative to protect your company’s sensitive data.
10 SSO Best Practices
- Know What SaaS Apps You Have
- Know Your Users—External Users Included
- Know Which SaaS Apps Can be Connected
- Connecting to your Azure AD or G-suite
- Develop an Automatic Provisioning Strategy
- Understand the Hidden Cost of SSO
- Recognize Multi-Factor Authentication Side Effects
- Time to Configure and Connect SaaS apps
- Remember that SSO is Not a Silver Bullet
- Remember SSO is No Longer a Luxury
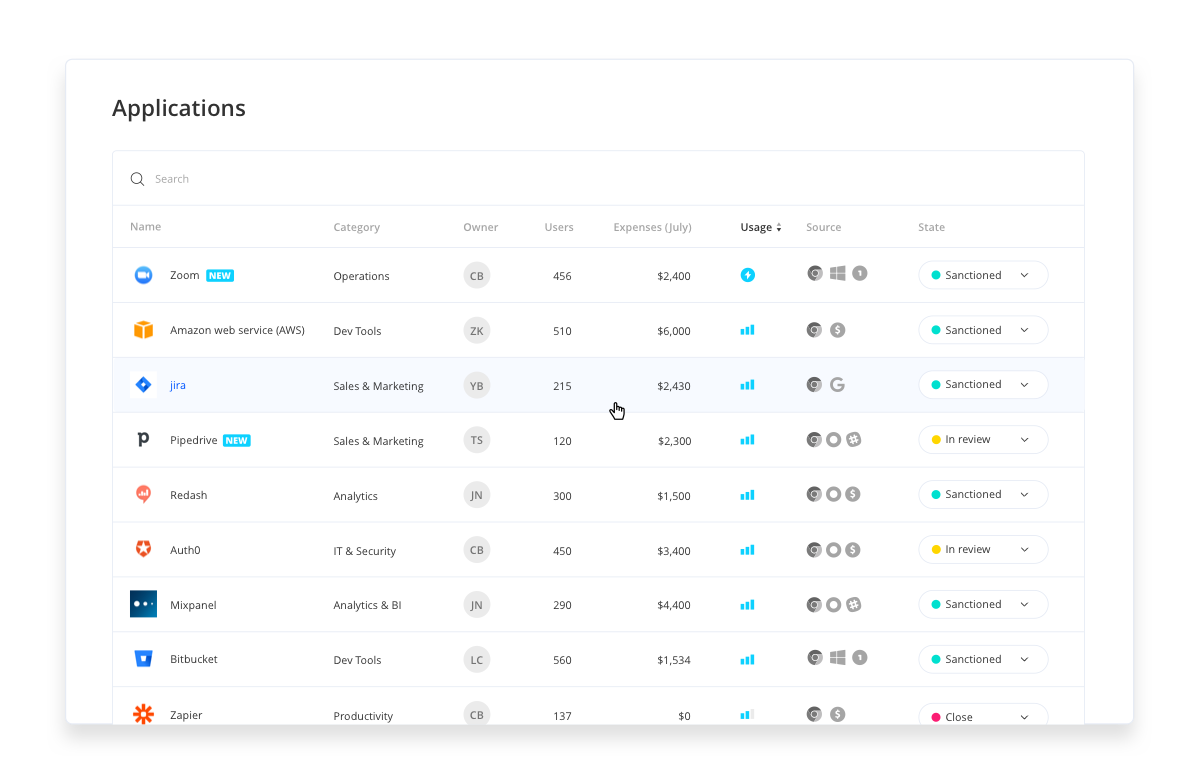
1. Know What SaaS Apps You Have
Before you implement an SSO it’s important to know what applications are used by your organization and which ones are just taking up space (and financial resources).
While mapping out your organization’s tech stack might appear simple, you may soon discover an array of unused, outdated, and even risky applications—all sitting outside of IT’s purview (the ever-growing problem of Shadow IT).
In fact, we’ve found that there is sometimes a 3x – 6x difference between perception and reality when it comes to IT’s estimates of how many applications are part of their SaaS Stack. That means for every 10 apps IT reports, the reality might actually be 30 – 60 apps.
This number may appear jaw-droppingly high but is actually pretty common in organizations missing a SaaS management tool. Saas Management tools remove the threat of Shadow IT, automating your tech stack’s mapping process by immediately granting your IT department full visibility to all SaaS applications used by your organization (even the ones currently outside of IT’s control).
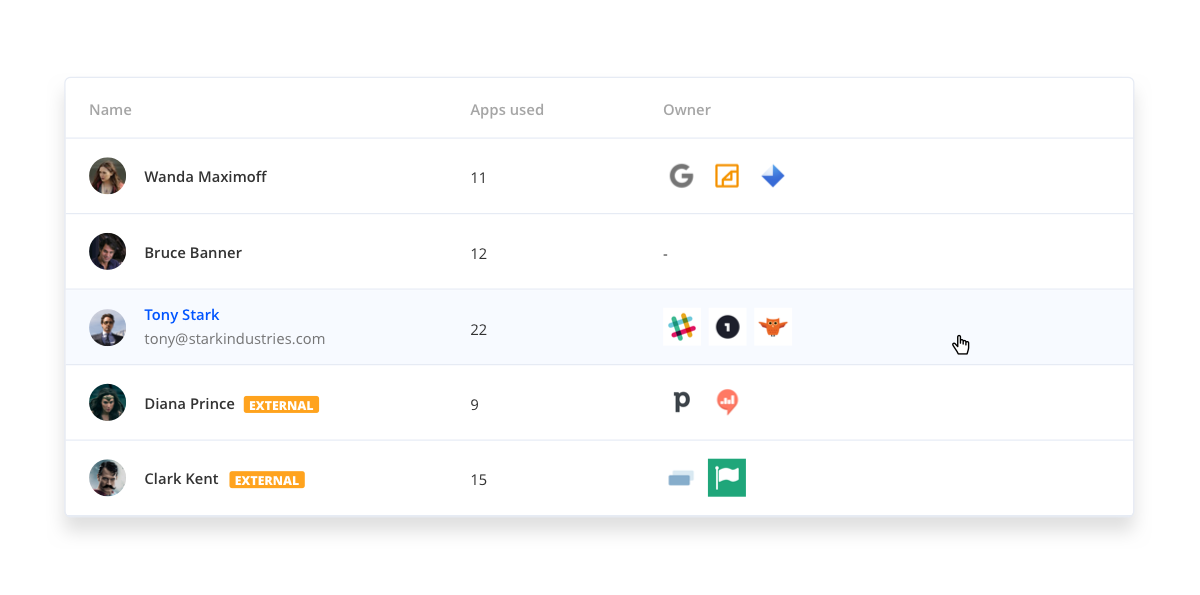
2. Know Your Users—External Users Included
After you’ve mapped your SaaS applications, you need to understand who is using them, including internal and external users. External users are the contractors and temporary employees we tend to forget about when thinking of who needs access to our systems.
SSO best practice recognizes external users as invaluable assets to our organizations, but also acknowledges the security risk that comes with working primarily outside of the organization. Therefore, it’s recommended that employers provide external users with the same level of ease and security when accessing their systems—aka providing them with SSO logins.
3. Know Which SaaS Apps Can be Connected
Not all SaaS applications support Single Sign-On. Instead, only the SaaS applications with SAML 2.0 can enable this feature.
What is SAML 2.0? Security Assertion Markup Language 2.0 (SAML 2.0) is a standard for exchanging authentication and authorization data between security domains. SAML 2.0 enables web-based, cross-domain single sign-on (SSO), which helps reduce the administrative overhead of distributing multiple authentication tokens to the user.
To understand the full capabilities of your tech stack, you should begin identifying which of your apps support SAML 2.0 when you originally map your applications.
Additionally, make sure to inquire about whether your intended solution offers alternative protocols or support form-based login options. These features will ensure a secure login process for your employees across all applications–even the ones missing SAML 2.0.
4. Connecting to your Azure AD or G-suite
It’s SSO best practice to confirm that your intended SSO solution is able to delegate authentication requests to your identity provider.
Many organizations rely on G-suite or Azure AD as their identity provider, while some may opt for a different Directory as a Service (DaaS) solution.
No matter your preference, connecting these tools will create a master record of your users’ identities, allowing IT to easily make edits to application provisions and further protect your organization’s sensitive data.
5. Develop an Automatic Provisioning Strategy
Some SaaS applications may offer automatic provisioning. But is this a necessary feature and should you even enable it?
Automatic provisioning isn’t as scary as it sounds. This feature simply allows you to add users to your SSO provider and place them within a relevant group (with specific security measures). Once completed, the added user will automatically gain access to all selected SaaS applications linked to your SSO solution upon their first login.
While this method may save you time, without an Automated SaaS management tool, the process of provisioning may cause your license management to spiral out of control. Adding a provisioned user to your SSO may automatically assign an additional paid license to your linked applications, making full transparency into the makeup and use of your tech stack a must-have.
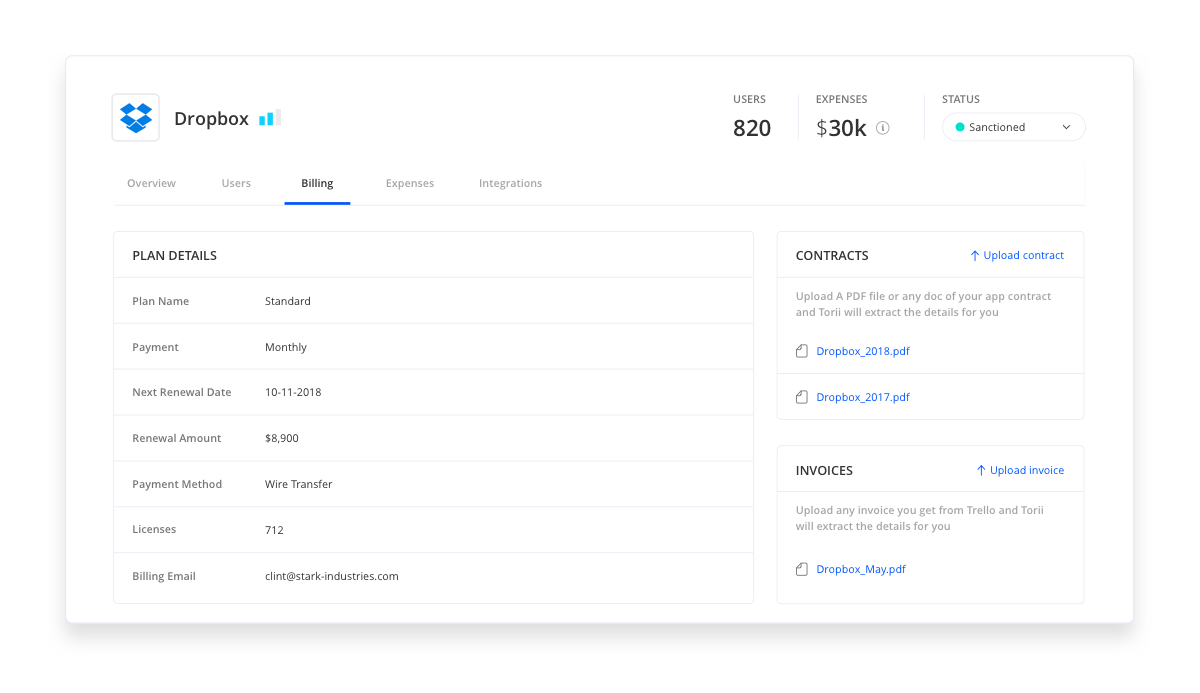
6. Understand the Hidden Cost of SSO
Remember our conversation regarding SAML earlier on? Well, making sure your SaaS applications can connect to your selected SSO solution may be costly.
It may come as a surprise, but many SaaS vendors do not offer SAML support in their basic offerings. Instead, they require organizations to upgrade their subscriptions to gain this feature.
Note 💡: The cost of these upgrades is not marginal, and in many cases, may even surpass the cost of your SSO provider.
Take Dropbox, for example. SSO support is enabled only for their Advanced plans. $20/user/month as opposed to $12.50/user/month on their Standard plan.
Using Zoom for meetings? Get ready to pay an extra $5 per user/month.
And if you want your user to log in to Slack using SSO, the price doubles from $6.67/user/month to $12.50/user/month.
These are just 3 examples and may not reflect the current state of your tech stack. Even so, it’s SSO best practice to understand your Saas vendor agreements, prospective upgrade costs, and plan your SSO budget accordingly.
7. Recognize Multi-Factor Authentication Side Effects
It is highly advised to add Multi-Factor Authentication (MFA) along with your SSO solution, or, at least, to your critical business applications.
MFA serves two important purposes: first and foremost, it adds a crucial layer of security, and secondly, it raises the security awareness of your employees.
But there’s a catch…some of your organization’s SaaS accounts may be shared, with more than one employee having access to them. Be aware that enabling MFA on certain business applications may block access to those shared accounts.
8. Time to Configure and Connect SaaS apps
Be aware that migrating your SaaS application to Single Sign-On takes time…yes, even when our SSO vendor promises a speedy implementation. SSO implementation goes far beyond clicking a few buttons.
In fact, there are several factors that contribute to the overall complexity of this process:
- Upgrading your SaaS application to the right plan, as discussed in number 6 – Understand the Hidden Cost of SSO.
- Configuring SAML for each SaaS application you’d like linked to your SSO (as discussed in number 3 – Know which Saas Apps can be Connected.
- Important: Configuring your SaaS apps is a manual process and each configuration will be different. The complexity of this process makes configuration an error-prone activity.
- Migrating from email/password login to SAML login may force all your users to reconnect. Some users may find themselves locked out of crucial business applications if they don’t follow all the guidelines. This may be a significant interruption to their workflow. To avoid this issue, make sure to communicate and educate relevant stakeholders about the login change well in advance.
9. Remember SSO is Not a Silver Bullet
Although SSO is a must-have for your security toolbox, like most tools, it is not a silver bullet.
SSO doesn’t replace your employees’ common sense and best practices on keeping SaaS applications secure.
Keep in mind, after an SSO system is implemented one password gives your employees access to all of the organization’s most valuable applications. Therefore, it’s important that your employees’ passwords are secure.
SSO best practice is to consistently educate your employees about securing their passwords, phishing scams, and other security threats. Plus, always remember to repeat the basics, reminding employees not to write passwords down on sticky notes or send them via email or Slack.
10. Remember SSO is No Longer a Luxury
The IT workplace is changing, and so is the role of the IT department. Providing your organization with the right set of tools to adapt to the ever-changing SaaS landscape while also keeping your sensitive data safe is crucial.
Implementing an SSO solution is no longer just a nice-to-have, but a need-to-have for any technological organization. Without it, your organization will be less secure, experience more bottlenecks, and will generally lag behind already optimized competitors.
Are you ready to secure your company’s sensitive data? Give Torii a try! It’s a simple and quick setup, and it gives you instant visibility and control over all your SaaS apps.

