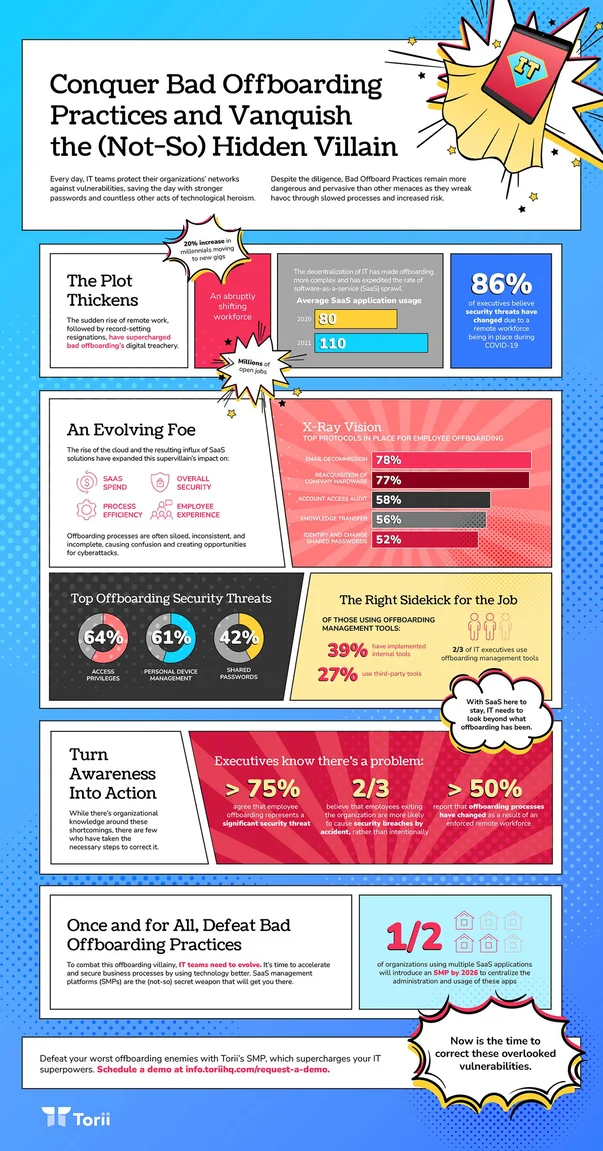
Security is (rightfully) top of mind for IT professionals. But, with public data breaches and tough-to-track threats weighing heavily on their minds, everyday security risks can fall through the cracks.
One looming example? Employee offboarding.
The SaaS era transformed the employee offboarding process. Gone are the days of simply collecting a past employee’s hardware, office keycard, and conducting an exit interview.
Today, IT also has to remove past employees from all of their organization’s applications.
Remote work and decentralized app ownership have put SaaS adoption in the hands of teams and employees, not IT, which is all good (and even great for company ingenuity) unless you’re the IT professional who has to support the offboarding process.
Now, IT also has to…
- Figure out what apps have been signed up for and/or used by the employee
- Revoke system access from Idp and SSO
- Close employee SaaS accounts
- Terminate VPN and review remote access methods
- Change system’s ownership
- And much (much) more
The list goes on and on, but you get the point.
Today, IT spends a lot of time and effort manually offboarding employees. This creates a large margin for error, leaving ex-employees with access to sensitive data and your organization with a huge liability on its hands.
It’s no wonder 76% of employees say that offboarding represents a huge security threat.
But don’t worry, this article isn’t just about the doom and gloom of employee offboarding (well, at least not moving forward). Instead, we offer employee offboarding solutions that minimize error while maximizing security (and efficiency!).
Swap Security Threats for Savings
Forgetting to revoke a past employee’s access privileges—especially for cloud applications—is like handing them keys to your company’s office.
Applications are the backbone of organizations. They harbor our sensitive data and critical IPs, and facilitate collaboration and productive work.
While most ex-employees wouldn’t intentionally cause harm, human error and accidental security policy violations can lead to a full-out security breach:
According to Torii’s data, every employee has access to ~30 different SaaS accounts, which should all be closed for security, compliance, and cost-saving reasons.
Even if your ex-employees steer clear of company data, their unused licenses are draining your organization’s SaaS budget (fueling Surprise SaaS Spend).
In fact, Torii found that unused licenses make up roughly 30% of organizations’ total SaaS license costs.
The bottom line is poor offboarding procedures, while avoidable, put your cyber security and budgets at risk.
With this in mind, we must remember a crucial point: Turnover is a natural part of the employee lifecycle. So, as long as your organization is up and running, employee offboarding will always be part of IT’s job description.
That’s why it’s important to implement a secure offboarding process.
Act and Automate—A Secure Offboarding Process
The best way to fix your offboarding process is to automate it with a SaaS Management Platform (like Torii).
With Torii, IT can easily define and automate all parts of the offboarding process, including:
- How access to an application (or group of applications) should be revoked
- Who is responsible for revoking access
- What the follow-up process will be
- What the confirmation process should look like
Once these offboarding workflows are established, Torii automatically deprovisions ex-employees from all applications.
I know what you’re thinking—All apps? What about Shadow IT?
Torii’s got you covered there too.
While many SaaS Management platforms can only automate (and identify) sanctioned applications, Torii’s discovery process finds all the apps used within your organization, even the ones never reported to IT:
Torii’s discovery process finds 2-3x more applications than other leading systems.
But that’s not all. With Torii’s One-click offboarding, users can also:
- Set up automatic reminders to follow up on different tasks and those of their colleagues
- Categorize costly and/or critical applications as crucial ensuring an ex-employee’s access is revoked to these apps before the offboarding process is tagged as complete
- Automatically enroll users into the offboarding workflow once they are marked by the HR department as departing or are removed from G-suite or an AD system
- Transfer an ex-employee’s data to their manager
- Notify an ex-employee’s manager once the offboarding process is complete
Not ready to fully automate the offboarding process just yet?
Within Torii’s offboarding dashboard, you can also configure the process and adjust as you go:
- Communicate with each application owner
- Delegate tasks and follow up on their status
- Gain a holistic view of which apps are revoked, by whom, and which ones still need attention.
Fix Your Offboarding Process with Automation
You know you need to fix your offboarding process, but most likely won’t solve the problem overnight.
In the meantime, Torii’s got you covered with a comprehensive IT Employee Offboarding Checklist.
Ready to automate your offboarding process? Read more about how Torii’s SaaS Management Platform accelerates user management while reducing operational risk.
![Worried About Security? Rethink Your Offboarding Process [Infographic]](https://www.toriihq.com/wp-content/uploads/2022/06/infographic-featured.jpg)
